What is Jabbercracky?
Jabbercracky is a community hash-cracking site designed for people of all skill levels. We host created hash-cracking events and challenges for players to crack. Jabbercracky is a fun and educational experience for all players. The event is free to play and open to everyone and designed to be accessible to players of all skill levels, from beginners to experts.
None of the hashes provided are real and are all generated for the purpose of the event. The hashes are designed with educational themes based on real-world cryptographic concepts and experiences. Under no circumstances would we use real hashes in the event. We go out of our way to ensure that all hashes are unique and provide a fun and challenging experience for all players. Our goal is to provide a safe and educational environment for all players to learn, and using real data would be a violation of that trust.
We believe that hash cracking is a foundational skill to cybersecurity, and those with skillz should be able to perform in our challenges regardless of their specialties. Finding ways to share the knowledge in a safe and encouraging way has always been our highest priority.
Disclaimer: Jabbercracky is a fictional event which is not based on any real-world event. Any similarities to real-world events are purely coincidental. Jabbercracky is intended for entertainment, educational, and research purposes only. View our full Privacy Policy and Terms of Service here.
What is Hash Cracking?
Hashes are the result of a one-way algorithm that transforms data into a fixed-length string of characters. Hashes are commonly used in cybersecurity to store authentication information, such as passwords. If the output of the hash function is the same for two inputs, then we likely have a match.
Hashes are used to protect sensitive information by ensuring that the original value cannot be easily read or recovered, but can still be verified. Hashes are different from encryption, as they are not designed to be decrypted. This makes “decrypted” the wrong term to use when referring to cracking hashes.
Hash cracking is the process of recovering the original value of a hash. This is done by comparing the hash to guessed plaintext values until a match is found. Hash cracking is commonly used in cybersecurity to recover secret material from hashed values and often involves the use of dictionaries, wordlists, and rules to generate potential plaintext values. Hash cracking is a common technique used in cybersecurity assessments and uses computational power to generate guesses.
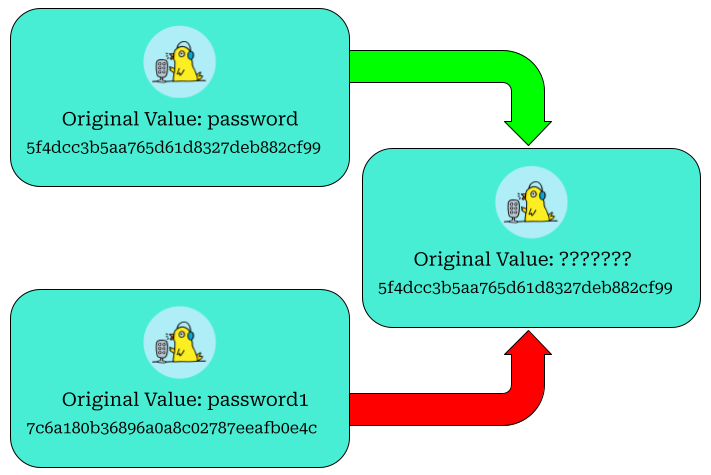 Concept of hash cracking
Concept of hash cracking
How are Points Awarded?
Players can get points by participating in cracking the hashes in the hash lists. Points are the same for every hash cracked, and gained points are used for loot rolls. The current point per crack amount can be found on the user's progress page.
Items are randomly rolled based on points gained per submission. The rarity of the items varies from rare to mythical. The more hashes that are cracked in a list, the higher the odds of receiving legendary loot. Items themselves are purely cosmetic and are generated randomly. Items can be equipped or sold for gold.
How Do Contests Work?
Jabbercracky is an event that runs throughout the year. Each event lasts for a limited time and consists of several hash lists that players can crack. Players can earn points, loot, and gold by cracking hashes and completing challenges.
Users can crack hashes while a contest is active or not. Use their rewards to get gold, which they can exchange for things for their account. Progress is kept as events change and the game repeats. The website uses three main phases to keep track of events: Inactive, Active, and Idle.
Inactive
Before an event starts, a countdown will appear signaling when the contest period will begin. The countdown is also on the /next-jabbercracky page, the login page, and the home page. While in this phase, all hash lists are available and users can continue to gain loot and points.
Active
When the countdown ends, the game will begin. When events start, the leaderboard and player inventory is temporarily reset, and only the latest hash lists are allowed to be submitted for points. Events are time-locked and at the end of the time limit, winners are announced. The countdown will show how much time remaining is left in the game period.
Idle
When an event ends, the game enters idle mode, where submissions are restricted and winners are announced. The game will remain in pause for twenty-four hours to allow users to collect data before it is merged back with the main game. Once idle mode ends, the game is reset back to inactive with all the contest data merged.
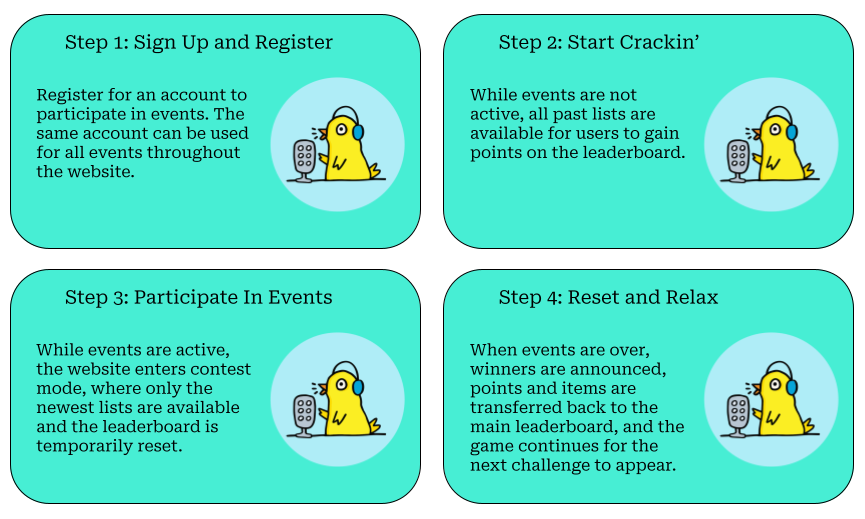 How to play Jabbercracky
How to play Jabbercracky
How are Winners Determined?
Winners are determined based on the total points accumulated during the event. The top players of a leaderboard-eligble event are awarded the prestigious honor of being on our all-time winner's leaderboard. This leaderboard will persist as events are reset so that players can see their past glory.
When events are not active, founds, items, points, and gold are all carried back to the main game and the game continues for the next event. When there are no events, all previous hash lists are available for users to download and work on. Players can continue to gain loot while events are active or inactive.
Code of Conduct
We expect all players to adhere to a code of conduct that promotes a positive environment. Players are expected to treat each other with respect and to not engage in any form of cheating or unsportsmanlike behavior. We reserve the right to disqualify any player who violates this faith-based agreement.
Code of Conduct:
- Do not engage in any form of cheating or generally uncool behavior.
- Do not attempt to disrupt the event or the experience of other players.
- Do not use any form of offensive language in public names or communications with other players and organizers.
- Do not share answers with other players while an event is active.
- Do not share any materials from an event with non-players while the event is active.
- Do not solicit or accept help from non-players while an event is active.
When are Events?
Events are held throughout the year. The schedule for upcoming events can be found on the /schedule page. We aim to release new events the second Friday of every month and a competitive event every year.
FAQ
Q: Are the hashes real?
A: No. None of the hashes provided are real and are
all generated for the purpose of the event. Under
no circumstances would we use real hashes in the event.
Q: What Time Zone Does Jabbercracky Use?
A: Jabbercracky uses Coordinated Universal Time
(UTC) for all events and times. Please convert to
your local time zone. The server time can be
retrieved from /api/ping.
Q: How do I register for Jabbercracky?
A: You can register for Jabbercracky
here.
Registration is free and open to everyone. We
require that players select a unique username that
complies with our code of conduct.
Q: How do I change or reset my password?
A: We offer a password reset feature here with the password reset token provided on registration.
Q: Can I recover my password reset token?
A: No. Password reset tokens are given on
registration and after password resets. If you lose
your token, you will not be able to reset your
password.
Q: How do I change my username?
A: You cannot change your username. If you need to
change your username, you must create a new account
with the desired username.
Q: How do I delete my account?
A: You can delete your account from the account
settings page.
Q: Do you delete inactive accounts?
A: Yes. We use automatic deletion for accounts that meet certain criteria:
- Accounts that have not logged in will be deleted automatically after two hours post registration.
- Accounts that have never submitted within 90 days of registration will be deleted.
Q: Do you sell my data?
A: We do not store any sensitive user data, and we
do not sell any user data. For more information,
please view our full Privacy Policy here.
Q: How could I contact the organizers?
A: You can contact the organizers by sending an
email to contact@jabbercracky.com.
Jabbercracky is a one-person operation, so please
be patient.
Q: When is the next event?
A: The contest schedule can be found on the /schedule page.
Q: What is Jabbercracky built with?
A: Go, HTML, and JavaScript.
Q: How are user passwords stored?
A: We use HMAC-Bcrypt with 8192 iterations.
Q: How is the authentication secret generated?
A: RSA 4096 is used to generate the authentication secret.
Q: How long is the authentication token valid?
A: The authentication token is valid for 720 hours (30 days).
Q: What submission formats are accepted?
A: The following submission formats are accepted:
multipart/form-dataapplication/json
Q: Are there any rate limits?
A: Yes. We have rate limits in place to prevent
abuse. If you exceed the rate limit, you will be
temporarily banned from the site for one hour.
- Registration and Logins: Once every few seconds
- Submissions: Once every 5 seconds and no more than 10 per 10 minutes
- 404 Errors: No more than 150 an hour
- 302 Errors: No more than 150 an hour
- 401 Errors: No more than 25 an hour
Q: Can I gain points from past events?
A: Yes. We maintain a catalog of past events and
the most recent hash lists are available for points
and loot until they are rotated out. The /past-jabbercrackys
page contains a list of all past events, including
those you can no longer gain points from.
Q: How could I keep my families, friends, and my passwords safe from password attacks?
A: For the everyday user, we recommend a few steps to keep passwords safe online and offline:
- Use a password manager to generate and store unique passwords for each account.
- Use Two-Factor (2FA) authentication where available.
- Use strong forms of Multi-Factor Authentication (MFA), such as hardware tokens or passwordless.
- For passwords you must remember, use a passphrase of four, five, or more randomly selected words separated by spaces, numbers, and special characters. Then modify selected words with transformations like leetspeak or alternating casing.